Works
Portfolio EKS
Portfolio
Building a Terraform-GitOps Integration for EKS with Argo CD
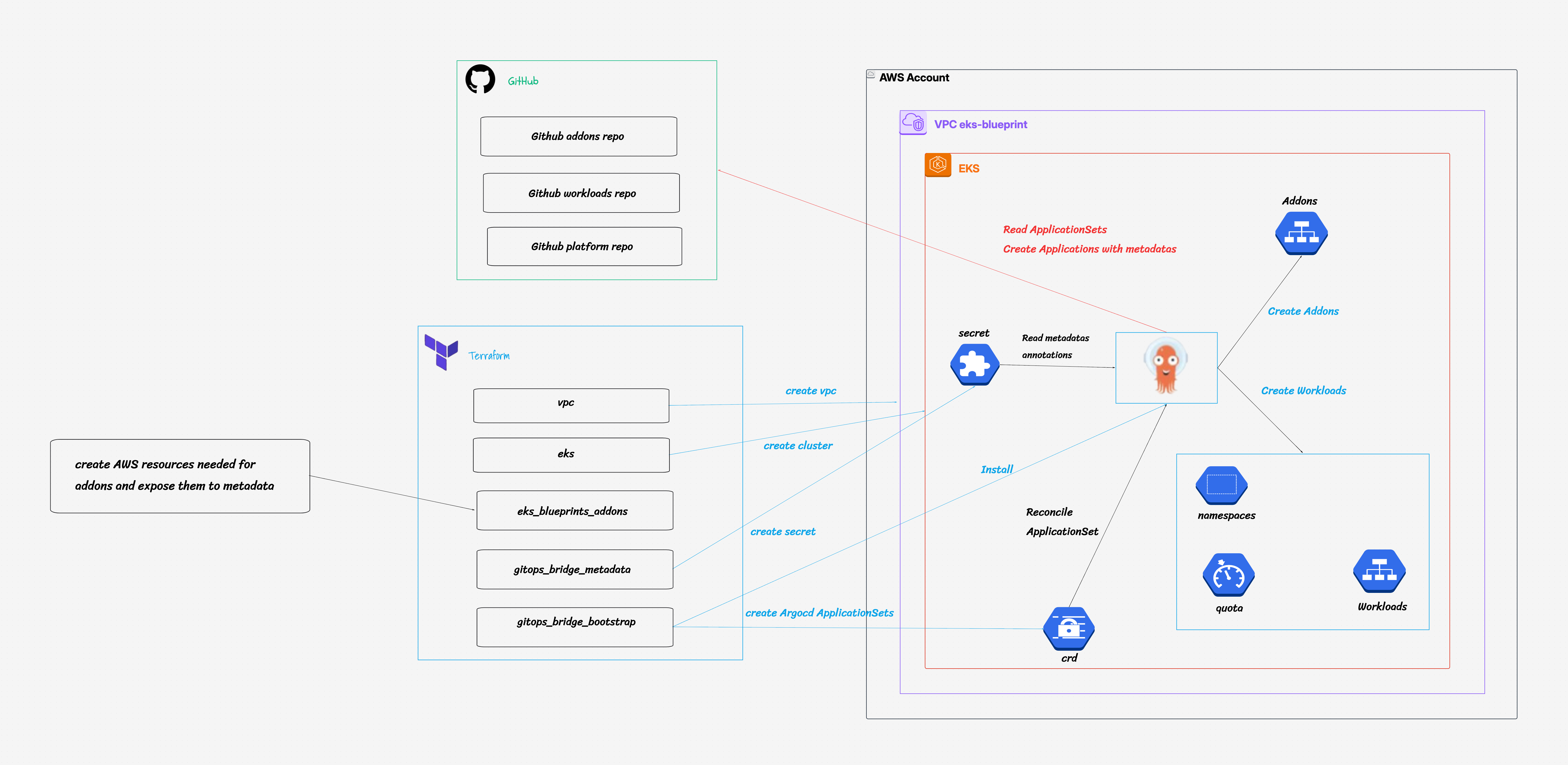
A comprehensive project involved provisioning secure and scalable Amazon EKS clusters using Terraform Blueprints, integrating Argo CD for GitOps-based deployment and lifecycle management of add-ons and workloads. The setup leverages the gitops-bridge-argocd-bootstrap Terraform module, dynamically passing cluster metadata to Argo CD for context-aware automation. Add-on installation is orchestrated using Argo CD ApplicationSets from the eks-blueprints-add-ons repository, enabling a fully automated, declarative, and scalable GitOps workflow.
• Provision Amazon EKS clusters with Terraform Blueprints, abstracting infrastructure complexity and promoting reuse across environments.
• Integrate Argo CD with EKS via the gitops-bridge-argocd-bootstrap module to dynamically extract and pass metadata from Terraform into Argo CD ApplicationSets.
• Delegate all add-on Helm chart installations to Argo CD, centralizing lifecycle management of Kubernetes add-ons via GitOps.
• Use terraform-aws-eks-blueprints-addons to define all add-on resources declaratively without installing them directly from Terraform.
• Automatically generate Kubernetes Secrets that include cluster metadata, allowing Argo CD to adapt its configurations dynamically at deployment time.
• Enforce GitOps principles for both infrastructure and application deployment, ensuring version control, rollback safety, and auditability.
• Empower application teams with autonomous deployment capabilities by abstracting platform configurations, allowing teams to deploy workloads independently while adhering to guardrails.
The architecture is built for automation, scalability, and team autonomy, consisting of:
𝗧𝗲𝗿𝗿𝗮𝗳𝗼𝗿𝗺 + 𝗔𝗿𝗴𝗼𝗖𝗗 𝗚𝗶𝘁𝗢𝗽𝘀 𝗕𝗿𝗶𝗱𝗴𝗲
• Enables automatic synchronization between Terraform-managed infrastructure and Argo CD-managed Kubernetes resources.
• Eliminates configuration drift by maintaining a single source of truth for infrastructure and workloads.
• Dynamically adapts Argo CD ApplicationSets based on real-time EKS cluster metadata passed via the gitops-bridge-argocd-bootstrap module.
• Separates concerns: Terraform handles cloud resource provisioning, while Argo CD manages Helm-based application lifecycle.
𝗘𝗞𝗦 𝗕𝗹𝘂𝗲𝗽𝗿𝗶𝗻𝘁𝘀 + 𝗔𝗱𝗱-𝗼𝗻 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁
• Platform team provisions consistent, secure EKS clusters using reusable and scalable Terraform Blueprints.
• Cluster-level add-ons (e.g., CoreDNS, Karpenter, ExternalDNS, ALB Ingress) are declaratively managed using Argo CD ApplicationSets sourced from the eks-blueprints-add-ons Git repository.
• Add-on deployment is version-controlled and cluster-aware, ensuring configuration consistency across environments.
• Streamlines operational workflows by decoupling infrastructure provisioning from application deployment.
• Promotes reusability and standardization, reducing operational overhead and human error.
GitOps-Driven Cluster and Application Lifecycle𝐬
• Infrastructure and workloads are defined declaratively in Git and synced automatically to the EKS cluster.
• Application teams can self-manage workloads via GitOps pipelines, while platform teams retain control over cluster-level configurations.
• Provides full auditability, rollback, and traceability for both infrastructure and application changes.
• Empowers DevOps collaboration by aligning infrastructure and application deployment in a unified pipeline.
Scalability, Security, and DevOps Best Practices
• All resources (IAM roles, networking, VPC, subnets, node groups, etc.) are provisioned securely via Terraform with minimal manual intervention.
• Cluster add-ons are installed in a context-aware manner, adapting automatically to specific cluster metadata.
• Built-in separation of environments (dev/stage/prod) ensures safe and scalable operations.
• Foundation for a fully automated, GitOps-based EKS platform aligned with modern cloud-native DevOps practices.
AWS Services and Tools Used
• Argo CD: GitOps tool to manage application deployment, addons deployment, namespace (limit range, RBAC, network policy, resource quota) creation.
• The GitOps Bridge: An open-source Terraform module designed to handle add-ons that require resources external to the Kubernetes cluster to operate correctly. Examples include:
• Terraform: Infrastructure as Code (IaC) tool for provisioning EKS clusters.
• Terraform Blueprints: A set of pre-defined Terraform configurations or modules that encapsulate best practices and standardized configurations for provisioning EKS clusters and addons.
• Helm: A package manager for Kubernetes that helps define, install, upgrade, and manage applications and services in a Kubernetes cluster by using chart templates that package all the necessary resources and dependencies.
• Kustomize: A standalone tool that lets us customize Kubernetes manifests through a declarative configuration approach without templates, using overlays to modify base YAML files with patches and transformers.
• Kube-Prometheus-Stack (Helm Add-on): deploys a full Prometheus monitoring stack (Prometheus, Alertmanager, Grafana, exporters, and Kubernetes monitoring CRDs) inside the EKS cluster for on-premises style observability of cluster and add-ons.
• AWS for Fluent Bit: A lightweight log processor that collects and forwards Kubernetes logs to CloudWatch Logs, enabling centralized, scalable logging for cluster add-ons and applications.
• CloudWatch Metrics for Kubernetes Add-ons: Automatically collects metrics from AWS-managed add-ons such as the VPC CNI plugin and Karpenter, enabling operational visibility and alerting through CloudWatch.
Best Practices for GitOps-Based EKS Platform Management
• Use Argo CD ApplicationSets to manage multi-cluster add-on installations declaratively.
• Integrate Terraform and Argo CD through dynamic metadata bridging to ensure seamless GitOps workflows.
• Separate platform and application responsibilities, allowing teams to operate autonomously but within secured boundaries.
• Standardize EKS provisioning using Terraform Blueprints to reduce drift and human error.
• Enable secure, scalable, and observable platforms by combining IRSA, CloudWatch, and GitOps principles.